DDoS: Permanent Flood of Data Without a Protection Strategy – And How To Protect Yourself Against It
The threat landscape around web applications and IT systems is becoming increasingly sophisticated. While traditional attacks such as SQL injections, cross-site scripting and session hijacking are still active in 2025, modern web frameworks, web application firewalls (WAF) and adherence to best practices have significantly mitigated them.
But have you ever heard of attacks that don’t involve stealing or manipulating confidential data? There are also attacks that are solely aimed at taking IT systems out of service for as long as possible and maximizing the damage to those affected.
In this article, we look at one such malicious attack method, which reached a new dimension in 2013 with the spamhaus.org spikes. 5 years later, GitHub experienced a DDoS attack with an almost unbelievable data rate of 1.35 Tbit/s. Such attacks are not isolated incidents — any company or organization could be affected tomorrow.
What are DDoS attacks?
DDoS stands for Distributed Denial of Service and describes an attack technique in which an enormous number of packets or requests are sent simultaneously to a target system in order to severely impair its availability or cause the system to crash. In contrast to classic DoS (Denial of Service), DDoS uses a group of compromised computers instead of just a single computer.
DDoS attacks can occur at different levels of the widely used OSI model, leading to a variety of attack possibilities. These can be broadly divided into two categories: blunt attacks and intelligent attacks, depending on which layer of the OSI model is the target.
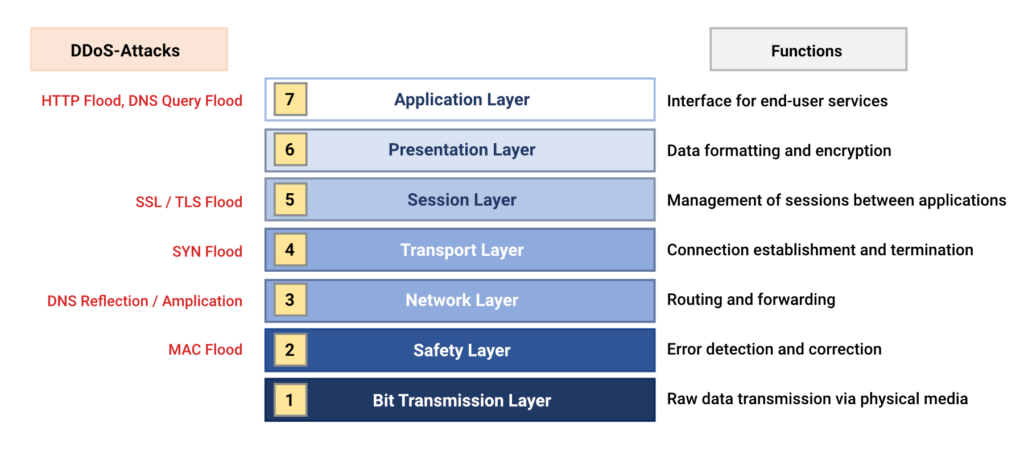
Attack methods: From simple to sophisticated
- SYN flood attack
A frequently used attack is the SYN flood attack, which is carried out at the transport level (layer 4). The attacker abuses the TCP three-way handshake that is used when establishing a connection between two computers. The attacker sends numerous SYN packets with falsified source IP addresses to the server, which responds with SYN-ACK packets. Since the last step of the handshake (ACK from the client) is omitted, the connections remain open and overload the system. Such attacks are relatively easy to carry out and can be fended off using techniques such as SYN cookies.
- DNS amplification (DNS reflection / amplification)
A far more sophisticated and harder to detect attack method is DNS amplification. In this method, the target system is flooded with DNS responses from legitimate DNS servers that it has never requested. Compromised computers in a botnet use publicly accessible DNS servers to make queries, the answers to which are then forwarded to the target via fake source IP addresses. The resulting data volume is often extremely high and can quickly overload the target system. In the case of the attack on spamhaus.org, this led to considerable disruption in global network traffic.
The damage caused by DDoS attacks
Whether simple flood attacks or sophisticated DNS amplification attacks — the damage caused by DDoS attacks can be enormous. In addition to direct sales losses and recovery costs, reputational damage and legal costs can also have considerable financial consequences.
Protective measures against DDoS attacks
To protect against DDoS attacks, it is important to develop proactive protection strategies. Here are some essential measures:
- Prioritize critical services
Determine which services are essential to your business, such as web applications, email servers or databases, and ensure that these are prioritized for protection.
- Use specialized DDoS protection services
Use services such as Cloudflare or Akamai that can protect your infrastructure from attacks and filter traffic.
- Implement intrusion detection systems (IDS)
Use IDS and centralized log analysis to detect anomalies early and respond to DDoS attacks.
- Create a DDoS response strategy
Develop a DDoS response strategy and train your team so that everyone knows what to do in the event of an attack. Regular testing will ensure that the plan works.
- Operate critical systems on a separate Internet uplink
Operating systems that are critical should be operated on a different Internet uplink in order to place them specifically under DDoS protection measures without affecting the entire infrastructure.
- Geographic traffic filtering
Configure your firewall to block or prioritize traffic from non-relevant geographic regions to reduce the pressure on your systems.
Advanced protection strategies: training and best practices
DDoS attacks are just one part of the wider threat landscape affecting web applications. To build lasting knowledge of security measures and arm yourself against modern threats, we recommend practice-oriented intensive training courses. These training courses cover a broad spectrum of attack techniques and defense mechanisms and offer you the opportunity to take targeted action against cyber attacks.
Conclusion: Protection against DDoS attacks
DDoS attacks are a serious threat to companies and organizations worldwide. However, with the right protective measures and a well thought-out response strategy, you can ensure that your systems remain functional even in the event of an attack and that the damage is minimized.
For even deeper expertise, we recommend iSAQB-certified web security training, which will equip you with the necessary skills to effectively protect your web applications.
Sources
- spamhaus history (retrieved on 14.09.2024)
- GitHub DDoS Incident Report (retrieved on 03.09.2024)
This is a translation of ITech Progress’ blog post “DDoS: Dauerhafte Datenflut ohne Schutzstrategie – und wie man sich davor schützen kann”. Here you can find the original blog post in German.






